The Business Central or Navision web client has grown up since the 2018 version! And it continues to grow. Since then, there has hardly been a good reason to use the Windows client. Since Business Central 2019 (Nav Fall Release 2018) (BC15), there is therefore no longer a Windows client. Simply open a browser, enter the URL and start working with Navision or Business Central immediately. Incidentally, even across company boundaries: the web client completely replaces remote access such as an RDP (Remote Desktop Protocol) client, Teamviewer, VNC and other remote access technologies!
Within a Windows domain, logging in via Windows is still the most convenient method and is supported by Navision as standard. Simply install Navision and Business Central as described here and off you go. Especially with the web client! If the browser asks for login data: Simply enter the Windows access data and you're done.
But what if you want to use the client remotely, outside a VPN, outside a Windows domain? Then there is no Windows access data to enter. Nothing easier than that: Change Navision to the credential type NavUserPassword, and... nothing works anymore!
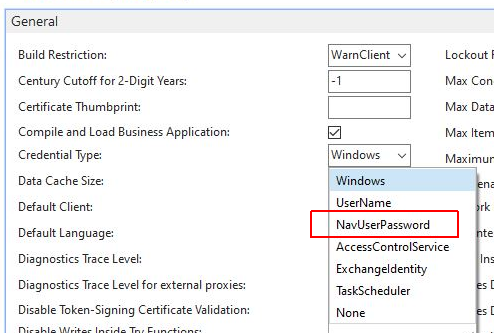
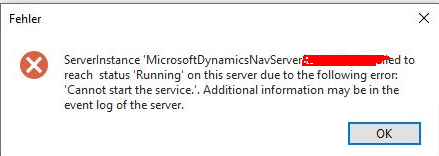
The solution is quickly found in the Event Viewer: Navision now requires a certificate! The event viewer reports the error:
Server instance: xxxx
Type: Microsoft.Dynamics.Nav.Types.NavConfigurationException
SuppressMessage: False
ContainsPersonalOrRestrictedInformation: False
DiagnosticsSuppress: False
MessageWithoutPrivateInformation: Certificate with the fingerprint was not found in the CurrentUser or LocalMachine memory.
Microsoft.Dynamics.Nav.Types.CertificateHelper.FindCertificateFromThumbprint(String certificateThumbprint)
Microsoft wants to protect the user from himself here, and in this constellation only authenticates via a certificate. Regardless of whether you want or need this additional security level. So roll up your sleeves and off you go. Also very easy since 2018 thanks to new Powershell scripts. The witches' dance with makecert.exe is no longer necessary!!
Attention! Important! The following certificate generation creates a so-called self-signed certificate, just as makecert.exe did previously. This works for the task described here. However, it does not work if you want to release the Navision or Business Central web services on the Internet! In this case, you absolutely need a publicly signed certificate, as you can obtain from various issuers and also from LetsEncrypt.
Note: You can also use any other available certificate, in which case please simply skip the steps for creating a new self-signed certificate. Otherwise, it is easiest to carry out the following steps on the Business Central or Navision database server.
Preparation: You need the Powershell script New-SelfSignedCertificateEx, which you can find here :
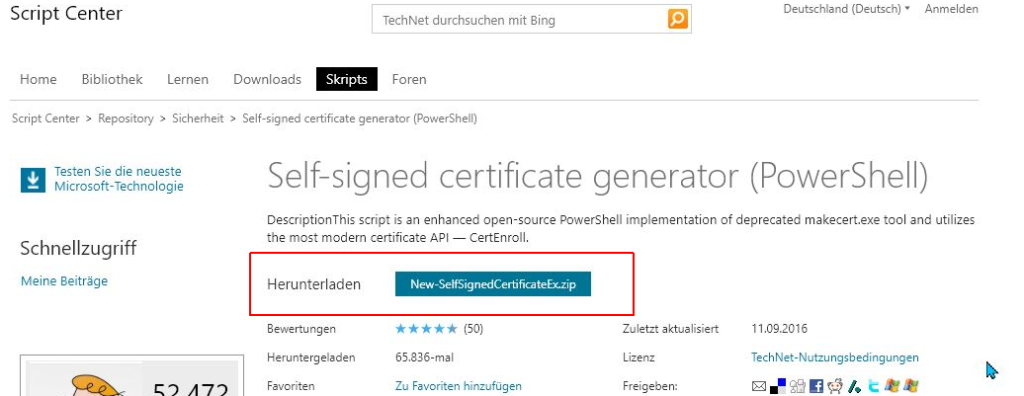
download and unzip this file e.g. to c:\Temp. I have attached the script here , but of course I recommend downloading it directly from Microsoft.
- Start the Powershell in administrator mode
- change to c:\temp (or where you have saved the script)
(Tip: You can type only the first letters of most commands and then complete them with the TAB key)
Set-ExecutionPolicy RemoteSigned
Confirm the query with Y - Import-Module .\New-SelfSignedCertificateEx.ps1
- New-SelfSignedCertificateEx -Subject „CN=Navision-Dienst“ -IsCA $True -Exportable -StoreLocation LocalMachine -FriendlyName „NavUserAndPassword“ -NotAfter $([datetime]::now.AddYears(5))
Of course, you can change the placeholders for the certificate name and password as you wish.
"Navision service" refers to the server name! At the end of these instructions you will find an option to change this name via the configuration files. Recommendation: Enter the correct DnsIdentiy right here! (computer name when installing Business Central or Navision).
Do not close the shell after the call, you still need the thumbprint.
This command creates a new certificate in the certificate store:
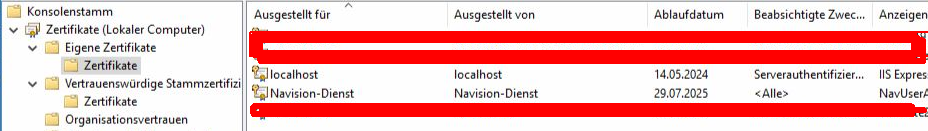
Open an mmc for the certificates (mmc.exe, File/Add SnapIn, Certificate, Computer Account/Local Computer).
Select the newly created certificate, right mouse click, All tasks, Manage private keys
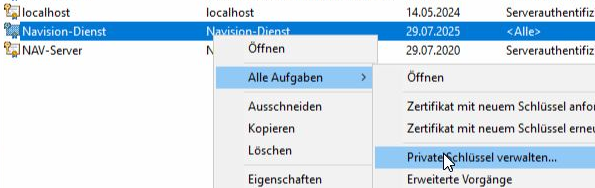
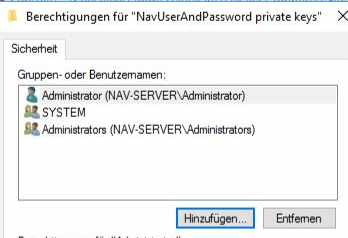
Add the service account of the Navision service server (often Administrator or Network/Network Services)
Please also copy the certificate to the Trusted Root Certificates/Certificates folder (right mouse button/copy, target folder -> paste)
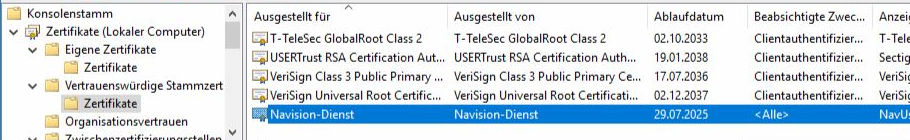
You can now close the certificate management.
Now copy the thumbprint from the console. This is more reliable than copying from the certificate management.
Now add this "fingerprint" (literally: thumbprint) to the Navision service configuration under Certificate Tumbprint:
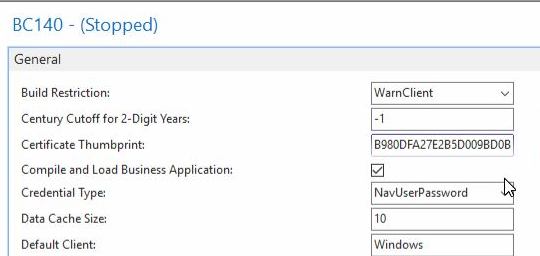
The computer name is stored in the certificate ("Navision service"). If this differs, you can alternatively change this in the:
Identity check error for an outgoing message. The expected DNS identity of the remote endpoint was "nav-server", but the remote endpoint has provided the DNS claim "Navision-Service". If this is a legitimate remote endpoint, you can resolve the issue by explicitly specifying the DNS identity "navision-service" as the Identity property of EndpointAddress when you create a channel proxy.
This is changed in the web.config (up to Nav 2017) or NavSettings.JSON in e.g. the folder C:\inetpub\wwwroot\Instance-Name, e.g. C:\inetpub\wwwroot\BC140 or ClientUserSettings.config in e.g. C:\Users\AppData\Roaming\Microsoft\Microsoft Dynamics NAV\100:
"//DnsIdentity": "The DNS or subject name from the server certificate.",
"DnsIdentity": "NAV-Server",Change the entry in Dns Identity from "NAV server" (in this example) to "Navision service": Recommendation: Create the certificate directly with the matching DNS entry!

